Joshua Wright talks to NPR about “Free Public WiFi” vulnerability
 Sunday, October 17, 2010 at 11:29AM
Sunday, October 17, 2010 at 11:29AM Joshua Wright talks briefly about the “Free Public WiFi”, adhoc network. This tactic has been around for a longtime. In fact, frequent travelers should be on the look out for hotel chain SSIDs in adhoc mode as well.
Depending on your configuration your wireless supplicant may connect automatically to these adhoc networks without you really knowing. Other times, the users sees a pop up “Free Public WiFi” and willingly connects to the network in hopes of free internet access. To the untrained eye these are wireless networks promising a free WiFi connection. However, you have no idea who is on the other end. The mobile user suspects it a real access point.
networks without you really knowing. Other times, the users sees a pop up “Free Public WiFi” and willingly connects to the network in hopes of free internet access. To the untrained eye these are wireless networks promising a free WiFi connection. However, you have no idea who is on the other end. The mobile user suspects it a real access point.
This NPR article stops by saying “it’s a bad thing and you should never connect”. But lets cover the why and the how. Suppose I configure an adhoc wireless network broadcasting the SSID “Free Public WiFi” from my laptop in a busy area where mobile users frequent. This could be at the mall, airport and conference center for example. The adhoc configuration is simple, so simple in fact it can be done in under a minute. You may recall a number of months ago the Russian spy’s were using adhoc wireless to communicate amongst themselves.
After I configure my adhoc wireless network. A non suspecting mobile user connects to me thinking they are getting FREE PUBLIC WiFi. But what they don’t realize they are connecting to my laptop. At which point I now have a layer 2 adjacency with this user. From here I could run a DHCP server on a VM local to my laptop. Whereby bridging layer 3 connectivity between me and the unsuspecting mobile user.
Once this is complete it’s a simple launch of Backtrack, whereby I could act as a man in the middle or deploy a library of attacks.
http://www.npr.org/templates/story/story.php?storyId=130451369
Wikipedia - http://en.wikipedia.org/wiki/Wireless_security
Security Tube - http://www.securitytube.net/Attacks-on-WiFi-(ADHOC-Networks)-video.aspx
Hot Spots Attacks - http://www.ethicalhacker.net/content/view/66/24/



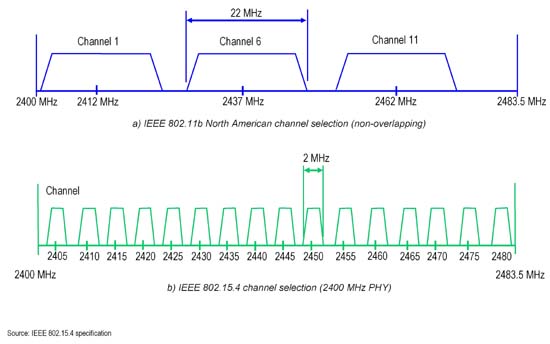
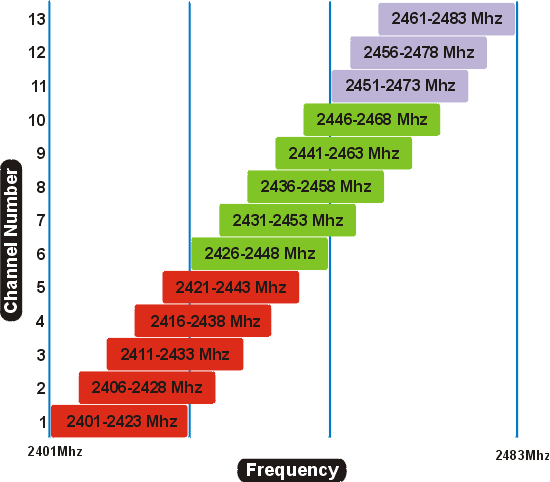

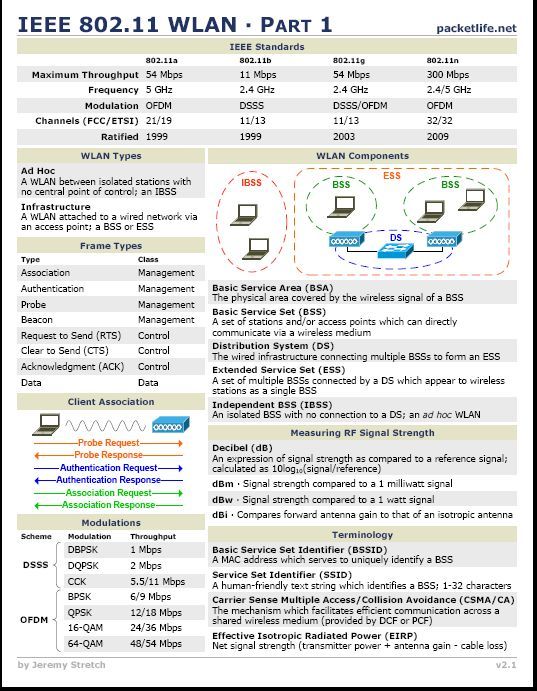
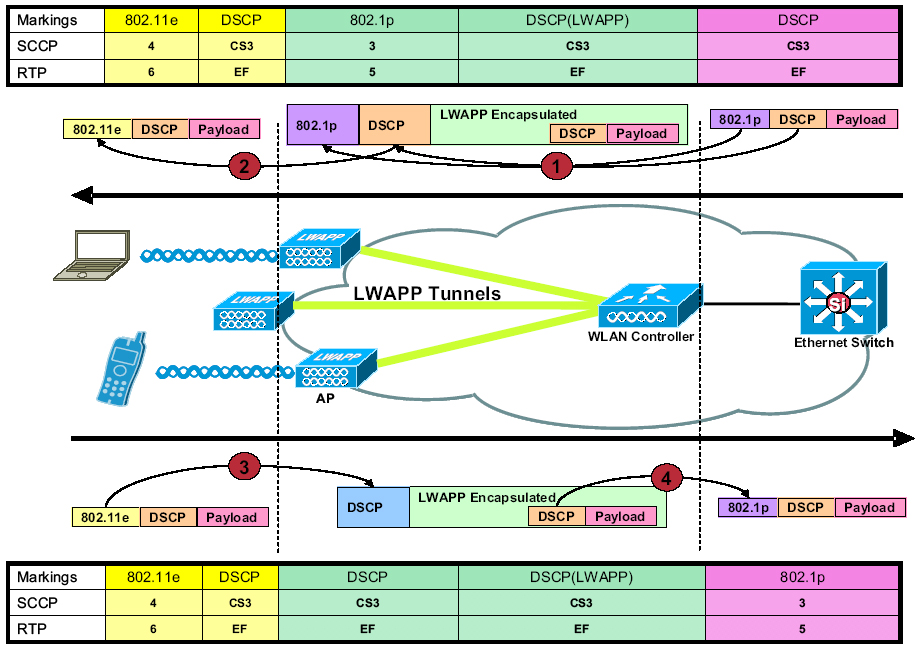
Reader Comments